This is as locked down as I have been able to get it on the external AWS account I am testing with:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:PutObject"
],
"Resource": "arn:aws:s3:::shotstack-s3-integration-au/*"
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:PutObjectAcl",
"s3:GetObjectAttributes",
"s3:ListBucket",
"s3:ListBucketMultipartUploads",
"s3:AbortMultipartUpload",
"s3:ListMultipartUploadParts"
],
"Resource": "arn:aws:s3:::*"
}
]
}
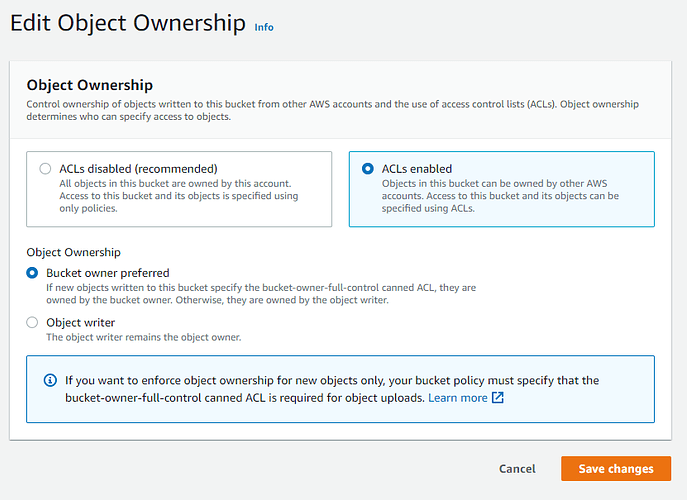
Also the bucket object ownership looks like this:
This is the best I have been able to do. If you need stricter controls there are a few things you can do:
- Create a separate AWS account for storing objects sent by us
- Copy the temporary URL we provide to you when the video/image finishes rendering and create your own script/process to copy the file to your S3 bucket. That way you do not need to provide us with credentials but you will have to code the copy function yourself.